Who Is Hacking My Phone? Unraveling the Mystery of Mobile Security Threats
In an era dominated by technology, our smartphones have become indispensable extensions of our lives. From personal conversations to financial transactions, our phones hold a treasure trove of sensitive information. However, with the increasing prevalence of cyber threats, the question that looms large is, "Who is hacking my phone?" In this in-depth exploration, we will dissect the landscape of mobile security threats, examine common tactics employed by hackers, and provide actionable insights to safeguard your digital life.
Understanding the Landscape of Mobile Security Threats
Before delving into the specifics of phone hacking, it's crucial to comprehend the diverse landscape of mobile security threats that users may encounter.
Types of Mobile Security Threats
1. Malware:
Malicious software, commonly referred to as malware, includes viruses, spyware, and ransomware. These programs can compromise your phone's security, leading to unauthorized access and data breaches.
2. Phishing Attacks:
Phishing involves tricking individuals into divulging sensitive information by posing as a trustworthy entity. Phishing attacks can occur through emails, text messages, or fake websites designed to mimic legitimate platforms.
3. Spyware:
Spyware is designed to secretly monitor and gather information about a user's activities. This could include tracking keystrokes, capturing screenshots, and accessing personal data.
4. Unsecured Wi-Fi Networks:
Connecting to unsecured Wi-Fi networks exposes your phone to potential threats. Cybercriminals can exploit vulnerabilities in these networks to intercept data and launch attacks.
5. SIM Card Swapping:
In SIM card swapping, attackers convince mobile carriers to transfer a victim's phone number to a new SIM card under their control. This enables them to intercept calls and messages, potentially gaining access to sensitive accounts.
Who Is Behind Phone Hacking? Unmasking the Culprits
The motivations behind phone hacking are diverse, ranging from financial gain to personal vendettas. Understanding the different actors involved can shed light on the tactics they employ.
1. Cybercriminals
Cybercriminals are motivated by financial gains. They may deploy malware or phishing attacks to steal sensitive information, such as credit card details or login credentials, which can be sold on the dark web.
2. Hacktivists
Hacktivists leverage hacking as a form of activism. Their motives often revolve around promoting a particular cause or ideology. Hacktivist attacks may involve defacing websites or exposing sensitive information to draw attention to their agenda.
3. State-Sponsored Actors
Governments or state-sponsored entities may engage in phone hacking for espionage, intelligence gathering, or to monitor political dissidents. Their capabilities often extend beyond those of individual hackers, employing advanced techniques.
4. Spies and Stalkers
In some cases, individuals may be targeted by spies or stalkers seeking to gather personal information for malicious purposes. This could include tracking location, monitoring communications, and accessing private data.
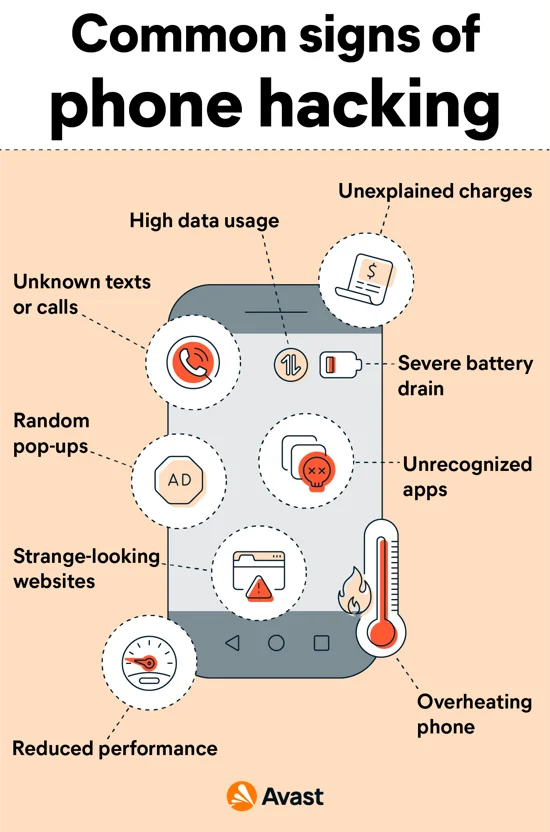
Signs Your Phone May Be Hacked: Decoding the Red Flags
Being vigilant about the signs of a compromised phone is crucial for timely intervention. Here are common indicators that your phone may be hacked:
1. Unusual Battery Drain:
Excessive battery drain could indicate the presence of background processes or malicious apps running on your phone.
2. Slow Performance:
If your phone suddenly becomes sluggish or unresponsive, it may be a sign of malware or spyware affecting its performance.
3. Unexpected Data Usage:
Unexplained spikes in data usage may suggest that your phone is transmitting information without your knowledge, possibly due to malware.
4. Unfamiliar Apps:
Check your phone for any unfamiliar or suspicious apps that may have been installed without your consent.
5. Strange Texts or Calls:
If you receive unusual texts or calls, or if friends report receiving messages from you that you didn't send, your phone may be compromised.
6. Overheating:
Malicious activities, such as background processes or unauthorized access, can cause your phone to overheat.
Steps to Protect Your Phone from Hacking: A Comprehensive Guide
Now that we've explored the threats and potential culprits, let's delve into actionable steps to protect your phone from hacking.
Step 1: Keep Software Updated
Regularly updating your phone's operating system and applications is crucial for patching security vulnerabilities. Developers often release updates to address known threats, and staying current is a proactive defense against potential attacks.
Step 2: Install a Reliable Security App
Choose a reputable antivirus and anti-malware app to provide an additional layer of protection. These apps can detect and remove malicious software, offering real-time scanning for potential threats.
Step 3: Use Strong and Unique Passwords
Create complex, unique passwords for your phone and all accounts associated with it. Avoid using easily guessable passwords and consider enabling two-factor authentication for added security.
Step 4: Be Cautious with Apps and Permissions
Only download apps from official app stores, and carefully review the permissions requested by each app before installation. Avoid granting unnecessary access to sensitive data.
Step 5: Enable Find My Phone and Remote Wiping
Activate features like "Find My Phone" or remote wiping options. These tools allow you to locate a lost device or remotely erase its data if it falls into the wrong hands.
Step 6: Avoid Public Wi-Fi for Sensitive Activities
Refrain from conducting sensitive transactions or accessing private information while connected to public Wi-Fi networks. If necessary, use a virtual private network (VPN) for added security.
Step 7: Regularly Check Your Accounts
Monitor your bank accounts, email, and other sensitive accounts for any suspicious activity. Timely detection of unauthorized access can prevent further compromise.
Conclusion: Empowering Yourself Against Phone Hacking
In the age of digital connectivity, safeguarding your phone from hacking attempts is a paramount responsibility. By understanding the diverse landscape of mobile security threats, recognizing potential red flags, and implementing proactive measures, you can significantly reduce the risk of falling victim to malicious activities.
So, the next time you find yourself asking, "Who is hacking my phone?" remember that knowledge and vigilance are your greatest allies. Stay informed, stay secure, and empower yourself to navigate the digital landscape with confidence.



.jpeg)