1. Introduction to Spynote: A Powerful Spy Tool
Spynote, developed by Hacker Yadav, is a formidable spy tool that has gained significant attention in the realm of surveillance and espionage. With its advanced capabilities and versatile features, Spynote enables users to remotely monitor and control targeted devices, intercept sensitive information, and discreetly record audio and video. This article explores the various benefits, installation process, ethical considerations, and best practices associated with using Spynote as a spy tool. Whether you are in the field of security, investigations, or simply curious about the capabilities of such advanced software, this article aims to provide valuable insights into the world of Spynote and its potential applications.
1. Introduction to Spynote: A Powerful Spy Tool
1.1 What is Spynote?
Spynote is not your ordinary tool for spying on your neighbor's cat (trust me, I've tried). It's a powerful and versatile spy tool that allows you to gain remote access and control over a target device. Think of it as your secret agent partner in the digital world.
1.2 Brief History and Evolution of Spynote
Spynote has come a long way since its inception. Born in the murky world of hacking, it has evolved over time to become a preferred tool for surveillance and espionage enthusiasts. It has seen significant updates and improvements, making it a force to be reckoned with in the world of sneaky spyware.
1.3 Popular Uses and Applications of Spynote
Spynote has found its way into various corners of the digital realm. From concerned parents keeping an eye on their mischievous teenagers to cybersecurity professionals testing the vulnerabilities of computer systems, Spynote has proven to be a valuable tool. Of course, we can't ignore the fact that it has also caught the attention of less noble individuals who use it for illicit purposes.
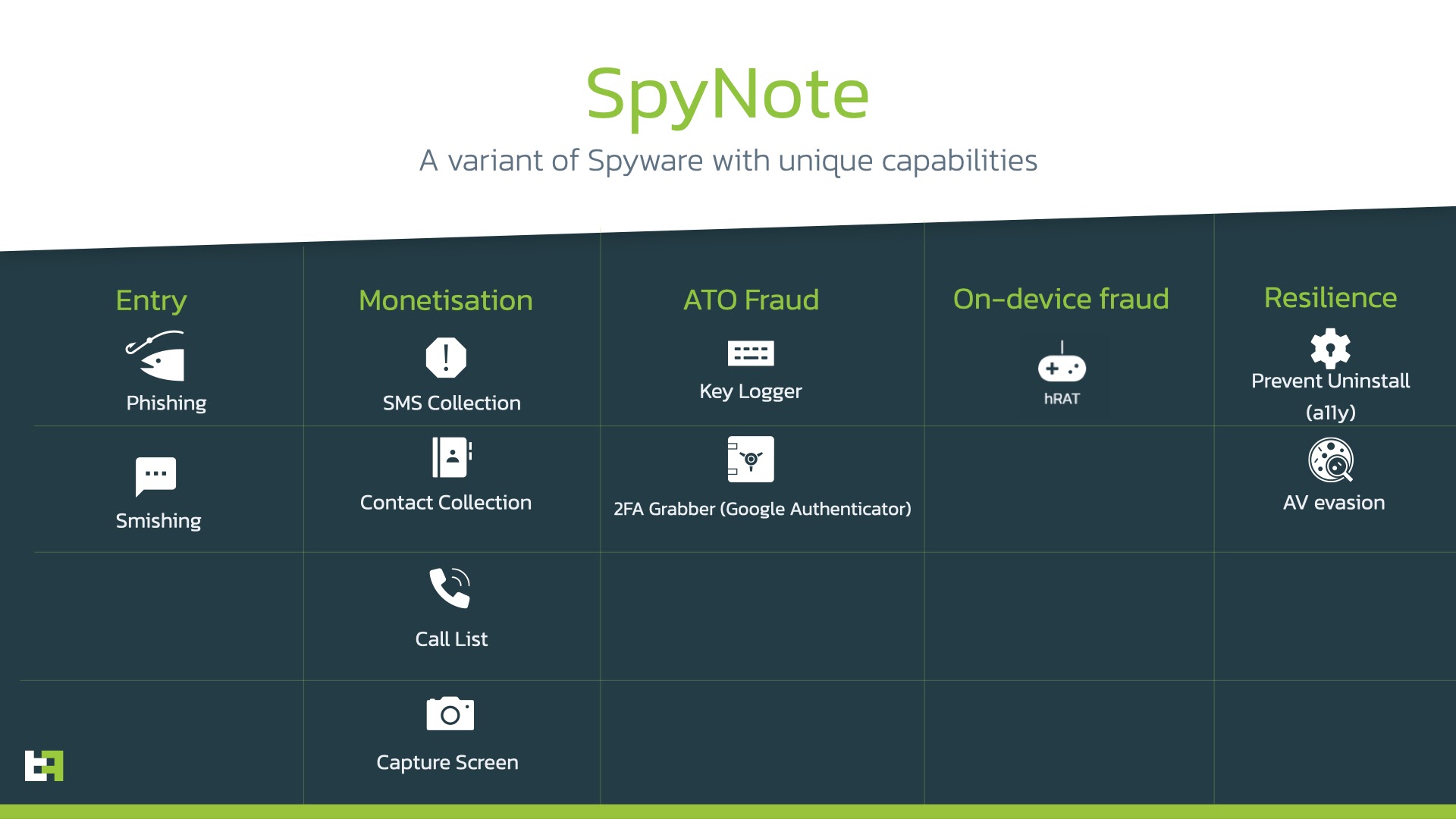
2. Key Features of Spynote for Surveillance and Espionage
2.1 Remote Access and Control
With Spynote, you can take control of a target device remotely, like a puppet master pulling the strings. From viewing files and browsing history to controlling the camera and microphone, Spynote gives you the power to snoop around undetected.
2.2 Stealing and Intercepting Sensitive Information
Spynote's abilities go beyond simple snooping. It's like having a virtual pickpocket in your pocket. It can steal sensitive information, such as passwords and credit card details, or intercept and read messages and emails without the target ever suspecting a thing.
2.3 Monitoring Communication Channels
Thanks to Spynote, you can become the ultimate eavesdropper by monitoring various communication channels. Whether it's WhatsApp, Facebook Messenger, or good old-fashioned phone calls, Spynote lets you have a sneak peek into private conversations without being invited to the party.
2.4 Secret Audio and Video Recording
If you've ever dreamt of being a secret agent, Spynote can make part of your dream come true. It allows you to discreetly activate the camera and microphone of the target device, turning it into your very own surveillance gadget. Just be careful not to accidentally record yourself singing in the shower.
3. Benefits of Using Spynote as a Spy Tool
3.1 Enhanced Surveillance Capabilities
Spynote takes surveillance to a whole new level. With its comprehensive toolkit of features, you can gather information and monitor activities with precision and ease. It's like having a top-notch spy agency at your disposal, minus the fancy gadgets and secret service budget.
3.2 Gathering Actionable Intelligence
Whether you're a private investigator uncovering a cheating spouse or a government agency tracking potential threats, Spynote helps you gather the crucial intelligence you need to make informed decisions. Just remember, with great power comes great responsibility.
3.3 Targeted Monitoring for Personal and National Security
Spynote can be a valuable tool in ensuring personal and national security. By monitoring and identifying potential risks or threats, it enables proactive actions to be taken. It's like having your very own digital guard dog, but without the barking or poop scooping.
4. Installation Process and Requirements for Spynote
4.1 Acquiring and Sourcing Spynote
Now, before we go any further, let's get one thing straight. I am here to provide you with information, not to endorse any illegal activities. Acquiring Spynote from legitimate sources and using it within legal boundaries is crucial. Remember, just because you can spy, doesn't mean you should.
4.2 System Requirements for Installing Spynote
To unleash the power of Spynote, you'll need a device that meets its system requirements. A compatible operating system, sufficient storage space, and a decent amount of RAM are essential to ensure smooth operation and avoid any unwanted crashes or glitches.
4.3 Step-by-Step Installation Guide for Spynote
Installing Spynote might require some technical know-how, so buckle up. A step-by-step installation guide will walk you through the process, ensuring you don't get lost in the labyrinth of codes and settings. Just remember, with great power comes great responsibility, and also the ability to accidentally delete your own files if you're not careful. So proceed with caution.
Disclaimer: The information provided here is for educational purposes only. The use of Spynote or any spy tool for illegal activities is strictly prohibited. Always respect privacy and follow legal guidelines. Don't be that person who ruins it for everyone else..3 Regular Updates and Maintenance
8. Final Thoughts and Disclaimer
8.1 Embrace Responsibility and Ethical Use
8.2 Use at Your Own Risk
5. Ensuring Anonymity and Security while Using Spynote
5.1 Protecting Your Identity and Location
When using a powerful spy tool like Spynote, it's crucial to prioritize anonymity and security. To safeguard your identity and location, consider using a virtual private network (VPN) to mask your IP address and encrypt your internet traffic. This can help prevent anyone from tracing your activities back to you. Additionally, be mindful of the Wi-Fi networks you connect to and avoid using public or untrusted networks that may compromise your privacy.
5.2 Secure Communication Channels and Data Encryption
To ensure the confidentiality of your communications, it's essential to utilize secure communication channels and encrypt your data. Spynote provides features that enable encrypted messaging and file transfer, but it's important to also consider the security of the receiving end. Encourage the use of strong passwords and end-to-end encryption for all parties involved in the communication to mitigate the risk of interception or tampering.
5.3 Avoiding Detection and Countermeasures
When engaging in any form of espionage, detection is the enemy. To avoid detection while using Spynote, it's crucial to remain vigilant and employ countermeasures. Regularly update your spy tool to stay ahead of any security vulnerabilities that may expose your activities. Furthermore, familiarize yourself with common countermeasures used by potential targets and develop strategies to bypass them. Remember, staying one step ahead is the key to success.
6. Ethical Considerations and Legal Implications of Spynote
6.1 Ethical Dilemmas of Espionage and Invasion of Privacy
While Spynote has its capabilities, it is essential to reflect on the ethical dilemmas associated with espionage and invasion of privacy. Consider the implications of your actions and respect others' right to privacy. It's important to have a clear purpose and justification for using such tools and to use them responsibly, with the informed consent of all parties involved.
6.2 Laws and Regulations Surrounding the Use of Spy Tools
Before utilizing Spynote or any spy tool, it is critical to familiarize yourself with the laws and regulations governing their use in your jurisdiction. Different countries have varying laws regarding surveillance, privacy, and data protection. Ensure that your actions comply with the applicable legal framework and obtain any necessary permissions or authorizations to avoid legal repercussions.
6.3 Potential Consequences and Penalties for Misuse
Misusing spy tools like Spynote can lead to severe consequences and legal penalties. Engaging in unauthorized surveillance, invasion of privacy, or any form of illegal activity can result in criminal charges and significant fines. It's important to understand the potential consequences before using such tools and to respect the boundaries set by the law.
7. Tips and Best Practices for Maximizing Spynote's Effectiveness
7.1 Setting Clear Objectives and Targets
To maximize the effectiveness of Spynote, it's important to establish clear objectives and identify your target audience. Determine the specific information you aim to gather and the purpose behind it. By doing so, you can tailor Spynote's features and settings to focus on the most relevant data and increase your chances of success.
7.2 Proper Configuration and Customization of Spynote
Spynote offers a wide range of customizable features to suit your needs. Take the time to familiarize yourself with its settings and capabilities, and configure it accordingly. Adjust options such as stealth mode, notifications, and data synchronization to optimize your spying operations. Adapting Spynote to your specific requirements will ensure a more efficient and targeted approach.
7.3 Regular Updates and Maintenance
To stay ahead of potential vulnerabilities and maximize the performance of Spynote, it's vital to regularly update the software and perform necessary maintenance tasks. Keep an eye out for new versions and security patches released by the developers, as they often address software flaws or enhance functionality. Regularly maintaining Spynote will help ensure its reliability and improve your overall experience.
8. Final Thoughts and Disclaimer
8.1 Embrace Responsibility and Ethical Use
While Spynote provides powerful capabilities, it's important to use them responsibly and ethically. Respect the privacy and rights of others, and only employ Spynote for legitimate purposes with proper consent. Remember that real-life consequences can arise from your actions, so make informed decisions and behave in a responsible manner throughout your usage.
8.2 Use at Your Own Risk
Using spy tools like Spynote carries inherent risks, both legally and ethically. This article does not endorse or promote the misuse or illegal application of such tools. The information provided is strictly for educational purposes and to raise awareness about the potential benefits and considerations associated with spy tools. It is your responsibility to use Spynote or any similar tools at your own risk and in compliance with applicable laws and regulations.In conclusion, Spynote stands as a powerful and versatile spy tool, offering a wide range of capabilities for surveillance and information gathering. While it has its benefits, it is essential to approach the use of Spynote ethically and within the bounds of the law. By following proper installation procedures, ensuring anonymity and security, and adhering to ethical considerations, users can maximize the effectiveness of Spynote while minimizing potential risks. As technology continues to advance, it is crucial to stay informed about the evolving landscape of spy tools and their impact on privacy and security. With responsible use and a clear understanding of the legal implications, Spynote can serve as a valuable asset for those in need of advanced surveillance capabilities.
FAQ
1. Is using Spynote legal?
While Spynote itself is a tool developed for various purposes, the legality of its use depends on the jurisdiction and the specific activities it is employed for. It is crucial to familiarize yourself with the laws and regulations governing surveillance and privacy in your country or region before using Spynote or any similar spy tools.
2. Can Spynote be detected by antivirus software?
Spynote is designed to operate discreetly and avoid detection by antivirus software. However, there is always a possibility that antivirus programs may detect and flag Spynote as malicious activity. To minimize this risk, it is recommended to use Spynote on devices that do not have robust antivirus protection or utilize advanced techniques to bypass detection.
3. What are the ethical considerations when using Spynote?
Using Spynote for surveillance purposes raises important ethical considerations. It is essential to respect privacy rights and obtain proper authorization before monitoring someone's activities or intercepting their communications. Misuse of Spynote can result in severe legal consequences and ethical dilemmas. It is advisable to consult legal experts and adhere to ethical guidelines to ensure responsible and lawful use of this tool.
4. Can Spynote be used for legitimate security purposes?
Yes, Spynote can be used for legitimate security purposes, such as monitoring and protecting computer networks, identifying vulnerabilities, and conducting authorized penetration tests. However, it is crucial to obtain proper authorization and adhere to legal requirements when using Spynote in a security context to avoid any potential legal or ethical issues.